REST (representational state transfer) is an architectural style consisting of a coordinated set of constraints applied to components, connectors, and data elements, within a distributed hypermedia system.
Burp can test any REST API endpoint, provided you can use a normal client for that endpoint to generate normal traffic. The process is to proxy the client's traffic through Burp and then test it in the normal way.
Most attacks which are possible on a typical web application are possible when testing REST API's. In this example we will demonstrate a SQLi injection attack on an application using a REST API. The example uses a version of 'DVWS'. Find out how to download, install and use this project.
这是Burp Suite在种子 URL 里的浏览'hops'的最大数。0表示让Burp Suite只请求种子 URL。如果指定的数值非常大,将会对范围内的链接进行无限期的有效跟踪。将此选项设置为一个合理的数字可以帮助防止循环Spider在某些种类的动态生成的内容。. Read the below steps: Traceroute sends a UDP packet with a TTL = 1 from the source to destination. When the first router receives the UDP packet it reduces the TTL value by 1 (1-1=0) then drop the packet and sends an ICMP message 'Time exceeded' to the source.
Identifying an API and mapping the attack surface
In a white or grey box testing situation you may be presented with the API documentation. This information should ensure good coverage of the attack surface.
However, in a black box test situation you may not have been informed that you are testing a REST API. How, then, do we identify the underlying technology?
In our example, the API is accessed from the URL:

http://localhost/dvws/vulnerabilities/sqli/api.php/users/2
Additionally, we can use Burp Suite to intercept the response and identify information in JSON format.
JSON (JavaScript Object Notation) is the most common means of exchanging data using a REST API.
Another common language is XML.
The next step is to identify parameters.
In our example, the parameter we have identified is in the URL:
api.php/users/2
We can alter this parameter to display different results:
api.php/users/3
Testing the API
Send the request to the Repeater tab.
We can use the Repeater tab to send the request to the server, like we would when testing any any other web application.
We have already demonstrated altering the value to a different number. Ascertaining that the parameter has an effect on the application.
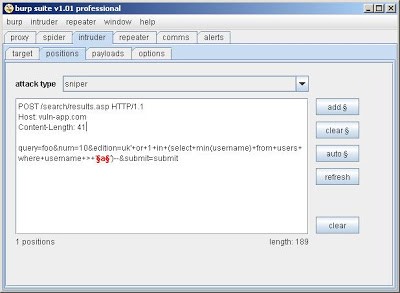
The next step is to detect that the parameter is being evaluated arithmetically.
We can enter a calculation in to the parameter and monitor the response from the server.
In this example, we supply the value 3-2 and the application returns the information for 'User/1' - 'Darth Vader'. The application is therefore evaluating the parameter arithmetically.
This behavior may point towards various possible vulnerabilities, including SQL injection.
The next step is to input SQL-specific keywords and syntax in to the parameter to compute the required value, thereby verifying that a SQL injection vulnerability is present.
A good example of this is the ASCII command, which returns the numeric ASCII code of the supplied character. In this example, because the ASCII value of the character 1 is 49, the following expression is equivalent to 1 in SQL:
50-ASCII(1)
The page is displayed without any errors and shows the details of 'user/1'. This is because the injected SQL syntax is equivalent to the value 1. This shows that the application is evaluating the input as an SQL query.
Burp Repeater is a simple tool for manually manipulating and reissuing individual HTTP and WebSocket messages, and analyzing the application's responses. You can use Repeater for all kinds of purposes, such as changing parameter values to test for input-based vulnerabilities, issuing requests in a specific sequence to test for logic flaws, and reissuing requests from Burp Scanner issues to manually verify reported issues.
The main Repeater UI lets you work on multiple different messages simultaneously, each in its own tab. When you send messages to Repeater, each one is opened in its own numbered tab. You can rename tabs by double-clicking the tab header.
Using Burp Repeater with HTTP messages
To use Burp Repeater with HTTP messages, you can select an HTTP message anywhere in Burp, and choose 'Send to Repeater' from the context menu. This will create a new request tab in Repeater, and automatically populate the target details and request message editor with the relevant details. Alternatively, you can open a new Repeater tab manually and select the 'HTTP' option.
For HTTP messages, each Repeater tab contains the following items:
- Controls to issue requests and navigate the request history.
- The target server to which the request will be sent is shown - you can click on the target details to change these.
- An HTTP message editor containing the request to be issued. You can edit the request and reissue it over and over.
- An HTTP message editor showing the response that was received from the last issued request.
Sending HTTP requests
When your request is ready to send, click the 'Send' button to send it to the server. The response is displayed when this is received, together with the response length and a timer (in milliseconds). You can use the usual HTTP message editor functions to help analyze the request and response messages, and carry out further actions.
HTTP request history
Each Repeater tab maintains its own history of the requests that have been made within it. You can click the '<' and '>' buttons to navigate backwards and forwards through this history and view each request and response. You can also use the drop-down buttons to show a numbered list of adjacent items in the history, and quickly move to them. At any point in the history, you can edit and reissue the currently displayed request.
Using Burp Repeater with WebSocket messages
To use Burp Repeater with WebSocket messages, you can select a WebSocket message in the Proxy history, and choose 'Send to Repeater' from the context menu. Alternatively, you can open a new Repeater tab and select the 'WebSockets' option.
For WebSocket messages, each Repeater tab contains the following items:
- A message editor containing the WebSocket message that will be sent. You can edit the message and resend it over and over.
- The WebSocket connection via which the message will be sent.
- A history table showing all of the messages that have been sent and received, and a message viewer for the message that is currently selected in the history.
Sending WebSocket messages
You can edit the message that will be sent, and select whether it should be sent to the server or client. Note that the option to send a message to the client is only available in connections that are still open via Burp Proxy.
When your message is ready to send, click the 'Send' button to send the message.
Burp Suite Kali Manually Send Request
Optionally, the history table will automatically select the next message that is received after you sent the message.
Burp Suite Send Multiple Requests
WebSocket message history
The history table shows all of the messages that have been sent and received. Messages that were generated manually within Burp Repeater are indicated in the 'Repeater' column. You can select a message to view it in the lower pane.
If you want to resend a message from the history, you can choose the 'Edit and resend' option on the context menu. This will show the selected message in the left-hand message editor, allowing you to modify the message as required, and then send it.
Repeater options
Burp Repeater has various options that control its behavior, including automatic updating of the Content-Length header, unpacking of compressed content, and the following of redirections. You can access these options via the Repeater menu.
Managing request tabs

http://localhost/dvws/vulnerabilities/sqli/api.php/users/2
Additionally, we can use Burp Suite to intercept the response and identify information in JSON format.
JSON (JavaScript Object Notation) is the most common means of exchanging data using a REST API.
Another common language is XML.
The next step is to identify parameters.
In our example, the parameter we have identified is in the URL:
api.php/users/2
We can alter this parameter to display different results:
api.php/users/3
Testing the API
Send the request to the Repeater tab.
We can use the Repeater tab to send the request to the server, like we would when testing any any other web application.
We have already demonstrated altering the value to a different number. Ascertaining that the parameter has an effect on the application.
The next step is to detect that the parameter is being evaluated arithmetically.
We can enter a calculation in to the parameter and monitor the response from the server.
In this example, we supply the value 3-2 and the application returns the information for 'User/1' - 'Darth Vader'. The application is therefore evaluating the parameter arithmetically.
This behavior may point towards various possible vulnerabilities, including SQL injection.
The next step is to input SQL-specific keywords and syntax in to the parameter to compute the required value, thereby verifying that a SQL injection vulnerability is present.
A good example of this is the ASCII command, which returns the numeric ASCII code of the supplied character. In this example, because the ASCII value of the character 1 is 49, the following expression is equivalent to 1 in SQL:
50-ASCII(1)
The page is displayed without any errors and shows the details of 'user/1'. This is because the injected SQL syntax is equivalent to the value 1. This shows that the application is evaluating the input as an SQL query.
Burp Repeater is a simple tool for manually manipulating and reissuing individual HTTP and WebSocket messages, and analyzing the application's responses. You can use Repeater for all kinds of purposes, such as changing parameter values to test for input-based vulnerabilities, issuing requests in a specific sequence to test for logic flaws, and reissuing requests from Burp Scanner issues to manually verify reported issues.
The main Repeater UI lets you work on multiple different messages simultaneously, each in its own tab. When you send messages to Repeater, each one is opened in its own numbered tab. You can rename tabs by double-clicking the tab header.
Using Burp Repeater with HTTP messages
To use Burp Repeater with HTTP messages, you can select an HTTP message anywhere in Burp, and choose 'Send to Repeater' from the context menu. This will create a new request tab in Repeater, and automatically populate the target details and request message editor with the relevant details. Alternatively, you can open a new Repeater tab manually and select the 'HTTP' option.
For HTTP messages, each Repeater tab contains the following items:
- Controls to issue requests and navigate the request history.
- The target server to which the request will be sent is shown - you can click on the target details to change these.
- An HTTP message editor containing the request to be issued. You can edit the request and reissue it over and over.
- An HTTP message editor showing the response that was received from the last issued request.
Sending HTTP requests
When your request is ready to send, click the 'Send' button to send it to the server. The response is displayed when this is received, together with the response length and a timer (in milliseconds). You can use the usual HTTP message editor functions to help analyze the request and response messages, and carry out further actions.
HTTP request history
Each Repeater tab maintains its own history of the requests that have been made within it. You can click the '<' and '>' buttons to navigate backwards and forwards through this history and view each request and response. You can also use the drop-down buttons to show a numbered list of adjacent items in the history, and quickly move to them. At any point in the history, you can edit and reissue the currently displayed request.
Using Burp Repeater with WebSocket messages
To use Burp Repeater with WebSocket messages, you can select a WebSocket message in the Proxy history, and choose 'Send to Repeater' from the context menu. Alternatively, you can open a new Repeater tab and select the 'WebSockets' option.
For WebSocket messages, each Repeater tab contains the following items:
- A message editor containing the WebSocket message that will be sent. You can edit the message and resend it over and over.
- The WebSocket connection via which the message will be sent.
- A history table showing all of the messages that have been sent and received, and a message viewer for the message that is currently selected in the history.
Sending WebSocket messages
You can edit the message that will be sent, and select whether it should be sent to the server or client. Note that the option to send a message to the client is only available in connections that are still open via Burp Proxy.
When your message is ready to send, click the 'Send' button to send the message.
Burp Suite Kali Manually Send Request
Optionally, the history table will automatically select the next message that is received after you sent the message.
Burp Suite Send Multiple Requests
WebSocket message history
The history table shows all of the messages that have been sent and received. Messages that were generated manually within Burp Repeater are indicated in the 'Repeater' column. You can select a message to view it in the lower pane.
If you want to resend a message from the history, you can choose the 'Edit and resend' option on the context menu. This will show the selected message in the left-hand message editor, allowing you to modify the message as required, and then send it.
Repeater options
Burp Repeater has various options that control its behavior, including automatic updating of the Content-Length header, unpacking of compressed content, and the following of redirections. You can access these options via the Repeater menu.
Managing request tabs
You can easily manage Repeater's request tabs. You can:
- Rename tabs by double-clicking the tab header.
- Reorder tabs by dragging them.
- Open a new tab by clicking on the right-most '...' tab.
- Close tabs by clicking the X button in the tab header.

